Passing your PCI Compliance audit isn’t enough. DataStealth gives you a single comprehensive platform that reduces PCI audit scope, protects payment pages from tampering, and liberates the ownership and control of payment card data and tokenization ensuring it stays where it belongs; with you.

DataStealth Payment Data Tokenization intercepts sensitive PANs before they land in your environment, replacing them with format-preserving tokens, and detokenizes only after they exit your environment.
The result? No payment card data is stored, processed, or transmitted in your environment, reducing the number of applicable PCI requirements, and the number of systems in scope for your PCI audit.
And all of this happens without the need for any changes to applications or systems, and without any API integrations.

Eliminate card data. Eliminate card data breaches.

Up to 95% fewer applicable systems/requirements for your PCI audit

Deploy without code changes, app rewrites, or API integrations

Works seamlessly across legacy, on-prem, and cloud environments
DataStealth eSkimming Protection stops all header and script tampering at the network layer, unlike competitors’ fragile browser scripts that can be easily stripped away. DataStealth validates every script and security header in real time, before it lands in the consumer browser, and blocks unauthorized code, ensuring compliance with PCI DSS requirements 6.4.3 and 11.6.1. DataStealth supports 100% of browsers and servers and ensures that every payment page served up is protected 100% of the time.
No code changes. No SDKs. No integrations.

DataStealth iframe Protection delivers a secure, fully hosted payment form that cannot be modified or replaced. Whether you use an internally built iframe, one from a TPSP, or a DataStealth-provided iframe, integrity is guaranteed. This combination of eSkimming Protection and iFrame Protection removes merchant-side card data exposure and eliminates the risk of client-side skimming, delivering bullet proof checkout security. The result? Uncompromising protection, effortless compliance, and peace of mind.

100% page and browser coverage 100% of the time

Block or alert attacks in real time, before any compromised page is delivered to a customer browser

Deploy without code changes, app rewrites, or API integrations

Works seamlessly across legacy, on-prem, and cloud environments

DataStealth Payment Card Discovery scans across on-prem, multi-cloud, and mainframe systems, including structured, and unstructured sources, to find payment card data wherever it may be hiding. PCI DSS requirement 12.5.2 requires that you confirm there is no payment card data anywhere but in your cardholder data environment (CDE). DataStealth makes this simple and automatic.

Surface every hidden card data store, whether on-prem or cloud

Schedule recurring scans to continuously monitor your environment and reduce manual effort.

Deliver clear, defensible evidence that no payment card data exists outside your CDE, meeting PCI DSS 12.5.2 requirements.
We’re not just compliant. We’re leaders. DataStealth is a PCI DSS Service Provider Level 1, a PCI SSC Participating Principal Organization, and a PCI SSC Board of Advisors member. We don’t just follow PCI standards. We help define them.

Automatically secure merchant-hosted or TPSP checkout forms. Protect revenue, and strengthen customer trust
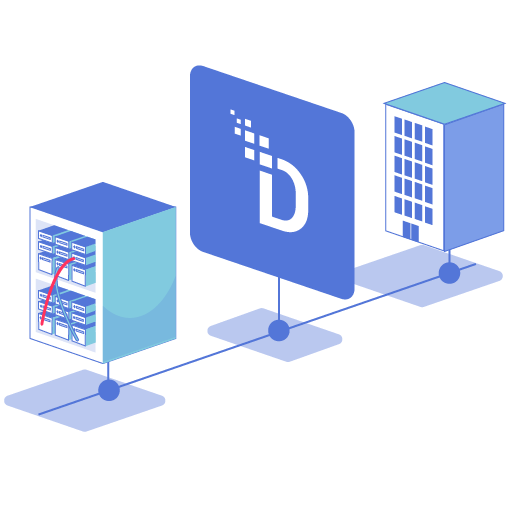
The DataStealth Data Security Platform centralizes discovery, protection, and compliance in a single solution

Shrink PCI scope by up to 90%, cutting audit costs, systems in review, and complexity.

With DataStealth, you own the data, and it works everywhere. Use tokens universally across gateways, processors, and partners, giving you the freedom to choose who you work with, and the leverage to control your payment processing costs.

As a PCI DSS Level 1 Service Provider, and a PCI Board of Advisors member, DataStealth is a trusted and proven authority when it comes to PCI Compliance.

Don’t just pass your PCI audit. Cut costs, reduce risk, and protect every transaction.
SCHEDULE A CALL