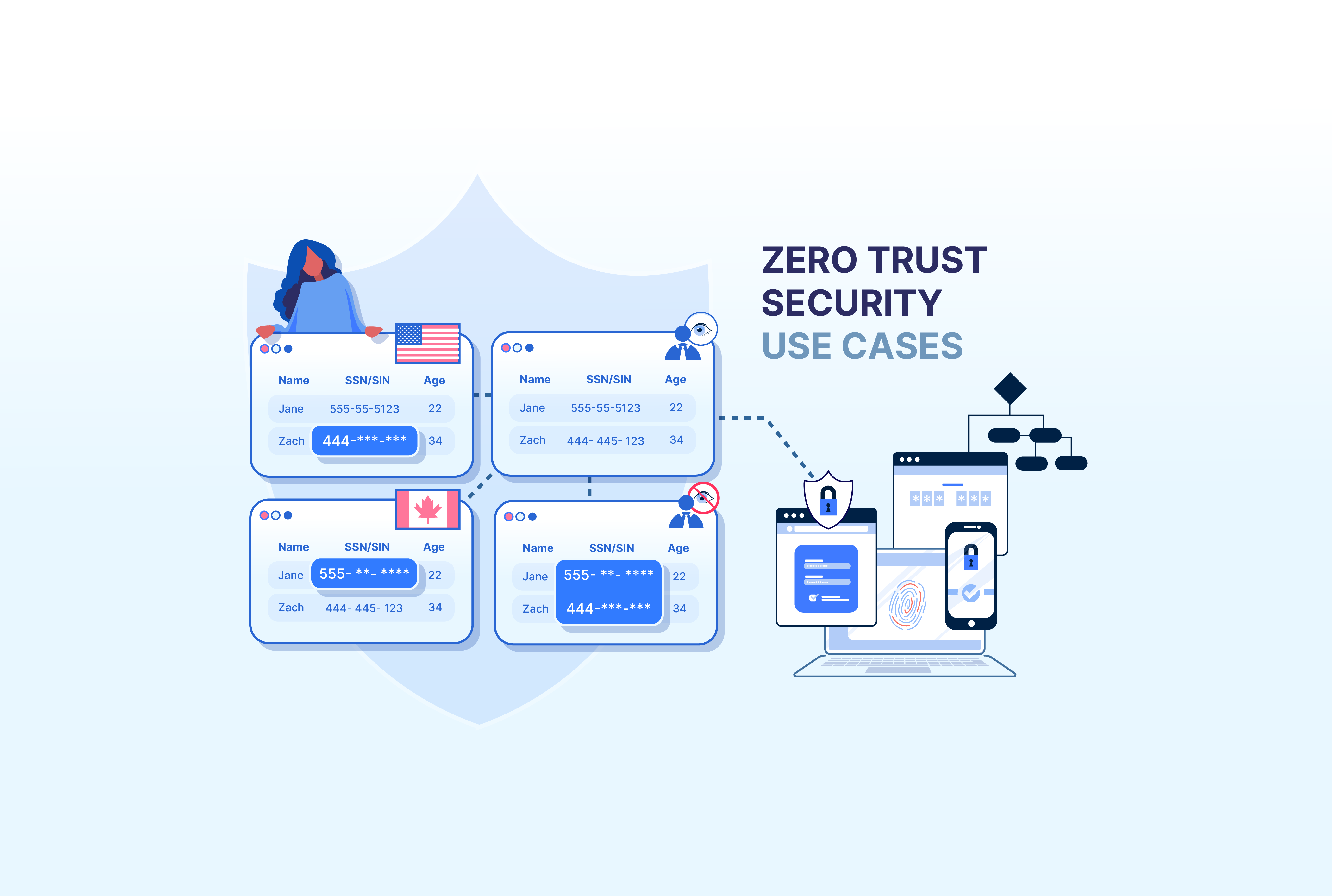
Data-centric Zero Trust secures sensitive data at the core using tokenization and masking, ensuring it's protected even if breaches occur. This approach minimizes compliance risk, supports safe data sharing, and enhances breach resilience across environments.
In today’s digital landscape, simply building higher walls around your network isn’t enough. The real prize for cybercriminals is your data, and unless you protect it directly, you’re still exposed.
That’s where data-centric Zero Trust comes in.
Instead of relying solely on perimeter defenses, this approach puts the security of your sensitive information at the core, protecting it with advanced techniques like vaulted tokenization and dynamic masking.
Even if attackers get past your outer layers, all they’ll find are substitute values or tokens they can’t make use of – not real data.
In this post, we’ll explore seven practical use cases for data-centric Zero Trust and show how you can safeguard your most valuable asset – your data – no matter where it lives or who needs to access it.
Zero Trust is a security model based on the principle of “never trust, always verify.”
This approach applies concepts such as least privilege, microsegmentation, and continuous verification at every layer of the technology stack.
It means moving beyond traditional perimeter-based security (which focuses on building thicker and taller walls) and, instead, applies the “never trust, always verify” principle to all resources – i.e., users, devices, applications, networks, infrastructure, and data.
Within the Zero Trust framework, organizations must prioritize protecting their data. It’s the main asset cybercriminals are targeting, and without directly protecting it, organizations are at risk of seeing the same gaps as traditional perimeter cybersecurity measures.
You can build more resilient walls, but unless directly protected, the data itself is vulnerable when breached, misused, or stolen. That’s where data-centric Zero Trust security comes into play; through vaulted data tokenization, the sensitive data is replaced with substituted values.
Even if your tokens get exfiltrated, attackers can’t do anything with them, no matter what tools they have at their disposal, including quantum computing.
Being ‘data-centric’ means that you’re working from the inside out; you’re starting by directly protecting the data so that, even in the event of a breach, it is fundamentally safe. You would then build around it, adding more resiliency with each layer while knowing that the core (i.e., the data) is safe no matter the case, even the worst case.
A data-centric approach allows organizations to enforce data residency and sovereignty requirements while still enabling business-critical functions, such as analytics and third-party integrations. This helps minimize regulatory risks and exposure from third-parties and cross-border data transfers, freeing business teams to leverage the best tools to drive revenue.
Apply vaulted data tokenization to all sensitive data before it leaves the country or enters third-party platforms (e.g., cloud analytics, survey tools). Only the tokens are shared externally, making the data valueless when intercepted or accessed by unauthorized parties.
For instance, if a company uses a third-party survey tool that may not be hosted in the required jurisdiction, tokenizing sensitive customer data before sending it to the survey platform ensures compliance with the residency and sovereignty rules associated with that data.
Use data discovery and classification tools capable of scanning the network to find known and unknown data repositories. This system should precisely identify data subject to data residency or regulatory controls.
Pair this with vaulted data tokenization to ensure that those accessing the data outside of permitted data residency requirements – for example, offshore or remote employees – can only view tokenized or dynamically masked data.
For instance, a company might have outsourced customer support to offshore teams who need to see the last four digits of client credit card numbers to confirm a client’s identity. In such cases, the system will only show them masked or tokenized data, giving the offshore team access to the information they need to operate, nothing more.
The benefits of this approach include:
Data-centric Zero Trust helps streamline compliance work. It can mitigate the impact of any breach and allow business teams to explore new third-party tools, systems, and channels without necessarily expanding compliance risk.
Vaulted data tokenization can remove cardholder data (CHD) or other sensitive data from an organization's environment. This reduces the number of systems under scope for various compliance standards, like PCI DSS and others.
QA and development teams, as well as AI platforms, often require high-fidelity data. Using production data for these purposes presents a risk of sensitive data exposure and can lead to major compliance problems.
Vaulted data tokenization or synthetic data generation can create high-fidelity, de-identified test datasets from production sources while preserving referential integrity and analytical value.
This gives non-production teams “production-like” data to use for testing and development without exposing sensitive information.
Data discovery and classification tools can ensure that when users outside a certain jurisdiction or operating from a non-company device request sensitive data, they’ll only receive tokenized or masked data, thereby reducing risks such as insider threats or accidental data exposure.
Organizations can deploy a test data management solution directly integrated with their CI/CD pipelines to automate the provision of tokenized or synthetic data for quality assurance and AI/ML model training. These solutions can also offer self-service capabilities for developers and data scientists.
Compliance and regulatory measures, such as GDPR, increasingly require organizations to enforce complex data retention and deletion policies. Organizations also need to prevent breaches resulting from unauthorized or accidental access to expired data.
Implement vaulted data tokenization with lifecycle management. This ensures that tokens and their mappings to real data are deleted according to configurable retention policies (e.g., upon request, or 12 months after creation or last use), rendering the data irrecoverable.
Use data discovery and classification tools to identify which data fields and records are subject to specific retention or deletion requirements.
This approach will readily and credibly demonstrate strong compliance with ‘right to be forgotten’ mandates and prove a commitment to data minimization.
In addition, it will also reduce regulatory and legal risk by ensuring expired data cannot be reconstructed or accessed. This minimizes who can access the ‘real’ data, while providing everyone else with only tokenized data. It will also automate data retention and deletion policies, hence reducing manual errors and audit burden.
Today’s enterprise environments often span multiple clouds and on-premises systems, with a growing – and often uncontrollable – use of third-party applications and AI tools, leading to significant data sprawl.
This creates risks not only from malicious insider threats but also from well-intentioned workers sharing sensitive data with AI tools for efficiency gains, thereby potentially extending data ownership to third-party vendors.
Vaulted data tokenization ensures all sensitive data is stored and transmitted as tokens by default, with detokenization allowed only for authorized users or contexts.
Data discovery and classification continuously scan environments to find new or unknown data repositories and enforce protection dynamically via tokenization and/or dynamic data masking.
Dynamic data masking offers real-time, policy-driven masking or partial reveal of data based on user attributes, device, location, and other risk signals, thus supporting both Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) models. This means access control decisions consider not just a user's role, but also the context of the access request, such as their location, time-of-day, or the device being used.
Third-party providers, including apps and services, are vulnerable to breaches. Even if an organization's own environment is secure, it cannot control the security posture of its vendors and partners.
Vaulted data tokenization ensures that these vendors and partners only receive substituted values (tokens), not the actual sensitive data. Therefore, even if a third party is breached, attackers cannot leverage the organization's actual data.
This approach ensures that the fallout from third-party supply chain breaches is mitigated by keeping your sensitive data out of those environments.
Organizations increasingly operate under an ‘assume breach’ mindset, an approach fully supported by data-centric Zero Trust..
Vaulted data tokenization ensures that environments, especially less secure ones like non-production or testing areas, only contain substituted values (tokens).
If attackers gain access to the tokenized data, they will find it to be valueless. Unlike encrypted data, which could potentially be decrypted with sufficient time and compute power (a risk amplified by emerging quantum computing capabilities), tokenized data remains secure.
This is because vaulted tokenization is quantum-resistant; there is no mathematical linkage between the original sensitive data and its tokenized representation. The substituted values are meaningless without access to the secure vault that stores the mapping between the token and the real data.
The key principle anchoring these Zero Trust use cases is that the data itself – the primary target of most cyberattacks – is inherently secured.
Vaulted tokenization enables an "inside-out" approach to securing data. This means that even if perimeter measures are bypassed and the protected assets are stolen, the impact is significantly less than if sensitive data itself had been stolen.
Adopting a data-centric approach is crucial for achieving Zero Trust, especially in the face of an evolving threat and technology landscape. Not being data-centric implies an organization is not adequately prepared to handle a breach, the likelihood of which is continually increasing.
In a way, one can argue that data-centric Zero Trust is the full manifestation of the Zero Trust philosophy: assume every entity accessing data is, by default, untrustworthy, and therefore provision only tokenized or masked data.
DataStealth is a data security platform (DSP) that fully integrates robust data tokenization, data discovery and classification, dynamic data masking, and test data management capabilities into one ready-to-use solution.
Experience a friction-free deployment that requires no code changes, agents and/or collectors. DataStealth is compatible across diverse environments, including unique and complex or even legacy systems, like mainframes.
Data-centric Zero Trust is no longer optional. Schedule a demo today to see how your organization can reduce breach risk, meet compliance goals, and future-proof sensitive data today.