Data masking is a technique used to protect sensitive data by replacing it with anonymized values that maintain the data’s structure and usability. Learn how data masking works and its role in enhancing data security and compliance.
Data masking, a powerful technique for protecting sensitive data, is increasingly adopted by organizations to ensure privacy, compliance, and operational efficiency.
This article explores the concept of data masking, its benefits, types, and why partnering with advanced solutions like Data Security Platforms (DSPs) is crucial for modern enterprises.
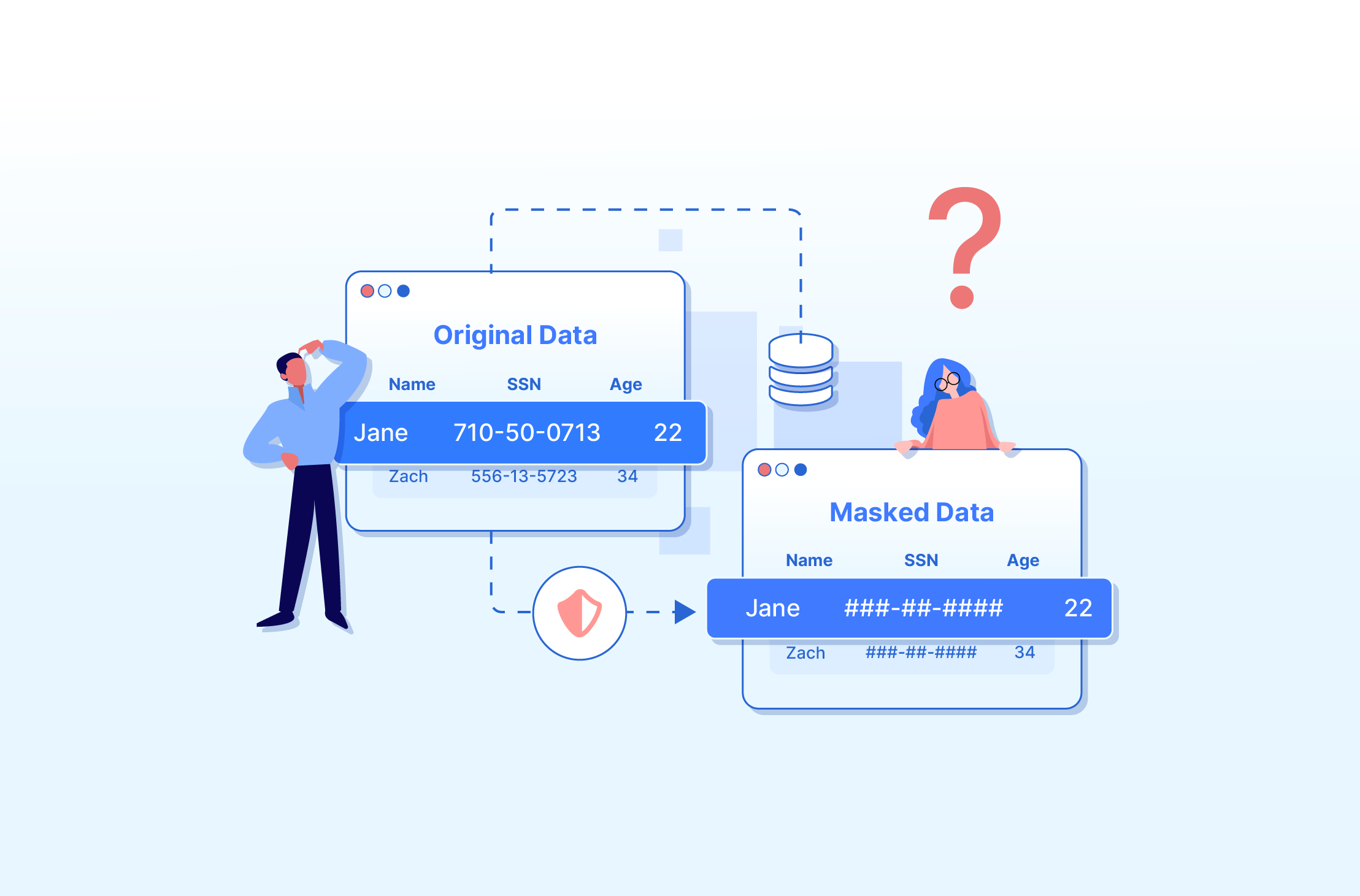
Data masking is a set of data security techniques used for protecting sensitive information - such as payment account numbers (PAN), personally identifiable information (PII), protected health information (PHI), financial details - and others from unauthorized access.
Data masking techniques can involve:
Data masking offers numerous benefits, primarily enhancing data security and compliance while preserving data utility. Below are a few examples of how different data masking techniques can keep your sensitive data across various contexts and situations.
Data masking protects sensitive information, either by redacting it or replacing it with de-identified values. With either data masking technique, organizations can reduce the risk of data breaches, insider threats, and unauthorized access.
Additionally, data masking helps organizations comply with stringent regulations like GDPR and HIPAA by anonymizing personal data, thereby minimizing legal risks and penalties.
Another significant advantage of data masking is its ability to support operational needs without compromising security.
For example, test data management (aka synthetic data) supports safe, but also realistic, testing environments for software development, allowing developers to work with functional datasets that closely resemble production without exposing sensitive information.
Moreover, it facilitates secure third-party collaboration by enabling organizations to share their masked datasets with vendors or partners without revealing sensitive details.
Furthermore, it supports cloud migration and analytics by ensuring that sensitive data remains protected during these processes while retaining its usability for analysis and decision-making.
Data masking also proves cost-effective by reducing the financial impact of potential breaches and simplifying compliance efforts.
Dynamic data masking (DDM) alters sensitive data in real-time as it is accessed, ensuring that unauthorized users only see masked values, while authorized users can view the original data.
This approach is particularly effective for role-based or attributes-based access control in applications such as customer support or medical record systems, where data security needs to be enforced on demand.
DDM operates without creating separate masked datasets by applying transformations at the time of query or access, which simplifies implementation in environments like cloud-based data lakes. It is increasingly used in combination with attribute-based access controls (ABAC) and data catalogs to streamline fine-grained data authorization.
Unlike static data masking (SDM), which creates separate masked copies of datasets, DDM applies masking dynamically at the time of access, making it ideal for zero-trust architectures and use cases where sensitive data must remain protected without duplicating or altering the underlying dataset. This approach suits organizations needing to enforce field-level data authorization while maintaining seamless operations across multiple applications or systems.
DDM is also advantageous for environments that prioritize operational efficiency and scalability. It eliminates the need to create and manage separate masked datasets, thus reducing storage requirements and operational complexity.
Additionally, DDM supports real-time compliance with region-specific privacy regulations by dynamically adjusting masking rules based on user roles or attributes.
Overall, DDM's ability to offer on-the-fly protection while integrating with advanced governance tools makes it a superior choice for dynamic, high-security enterprise environments.
SDM provides non-reversible methods for protecting sensitive data that involve permanently altering sensitive data before it is stored or shared, making it more suitable for non-production environments like software development and testing.
SDM ensures that masked data remains consistent across different environments by applying predefined masking rules during extraction, transformation, and loading (ETL) processes.
In contrast to DDM, SDM creates a separate masked dataset that can be safely shared without exposing sensitive information. This method is useful for compliance with privacy regulations or provisioning realistic test data.
However, when it comes to provisioning data for non-production environments, the most optimal data masking technique is test data management (or synthetic data) as it allows you to maintain the statistical properties of the original dataset.
Tokenization and format-preserving encryption (FPE) provide reversible methods for protecting sensitive data.
Tokenization replaces sensitive data with randomly generated tokens stored securely in a separate location, allowing the original values to be retrieved when necessary.
FPE transforms sensitive data into a secure format while preserving its structure, making it suitable for scenarios requiring reversible masking, such as compliance with financial regulations.
However, FPE is less flexible than traditional masking techniques when it comes to preserving the semantic or statistical properties of the original data.
Synthetic data (also called test data management) involves artificially generated datasets that mimic your real-world data while avoiding the privacy and security risks linked with using actual sensitive information.
This data masking technique allows organizations to create high-fidelity test data at scale in real time for non-production environments. Not only does this approach protect the original data, but it also gives testers an accurate representation of their users/customers, including the ability to maintain the statistical properties of the production dataset into the non-production environment.
Enterprise organizations should work with a Data Security Platform (DSP) when implementing any form of data masking due to the scalability, flexibility, and capabilities DSPs offer.
According to Gartner, DSPs simplify complex data authorization processes by integrating DDM with tools like ABAC, data catalogs, data discovery, and data classification solutions.
Moreover, Gartner states, “DSPs that integrate DDM with capabilities like data catalogs, ABACs and data classification solutions often.”
DataStealth offers multiple data masking solutions, giving you the ability to use the right data masking technique for your specific needs.
By working with DataStealth, you can leverage:
Interested in seeing our data masking solutions in action? Schedule a demo today!