
Learn how data protection platforms secure PII across cloud, SaaS, and legacy systems. Compare tokenization, encryption, masking, and top vendors.
Protecting sensitive data across hybrid environments, cloud workloads, and legacy systems is no longer optional; rather, it's a compliance requirement.
A data protection platform gives regulated industries a unified solution to discover, classify, mask, encrypt, and control sensitive data – without rewriting applications.
This guide explains what a data protection platform is, when you need one, and how to choose the right solution for your environment.
Data protection platforms help regulated industries:
The right platform depends on your environment complexity, performance requirements, and compliance needs. Agentless, network-layer solutions like DataStealth offer the fastest path to protection without application changes or integration overhead.
A data protection platform is enterprise software that secures sensitive data across databases, applications, cloud environments, and SaaS tools.
It combines multiple security functions into a single solution: data discovery, classification, tokenization, encryption, masking, and access control.
Key characteristics:
A data protection platform is different from a DSPM tool. DSPM tools find sensitive data. Data protection platforms neutralize it.
Regulated industries face strict data protection requirements under PCI DSS, HIPAA, GDPR, SOC 2, and CCPA. Non-compliance leads to fines, lawsuits, and reputational damage.
Three challenges drive adoption:
Sensitive data flows into Salesforce, Jira, Snowflake, Google Drive, and dozens of other systems. Without centralized protection, managing this data becomes manual, error-prone, and unscalable.
Development and testing environments often contain live production data. This exposes PII to developers, contractors, and third parties who don't need access to real customer information.
When attackers breach a system, the damage depends on what they find. If sensitive data is tokenized or masked, stolen data is worthless. Traditional encryption alone doesn't provide this protection because encrypted data with a compromised key is fully exposed.
Modern data protection platforms include these essential functions:
The platform scans databases, file systems, cloud storage, and applications to locate sensitive data. It then classifies data by type (PII, PCI, PHI), sensitivity level, and regulatory requirement.
Discovery happens continuously. New data is classified as it enters the environment.
Data masking hides sensitive values for non-production use. Masked data looks realistic but contains no real customer information. Developers can test applications without accessing actual PII.
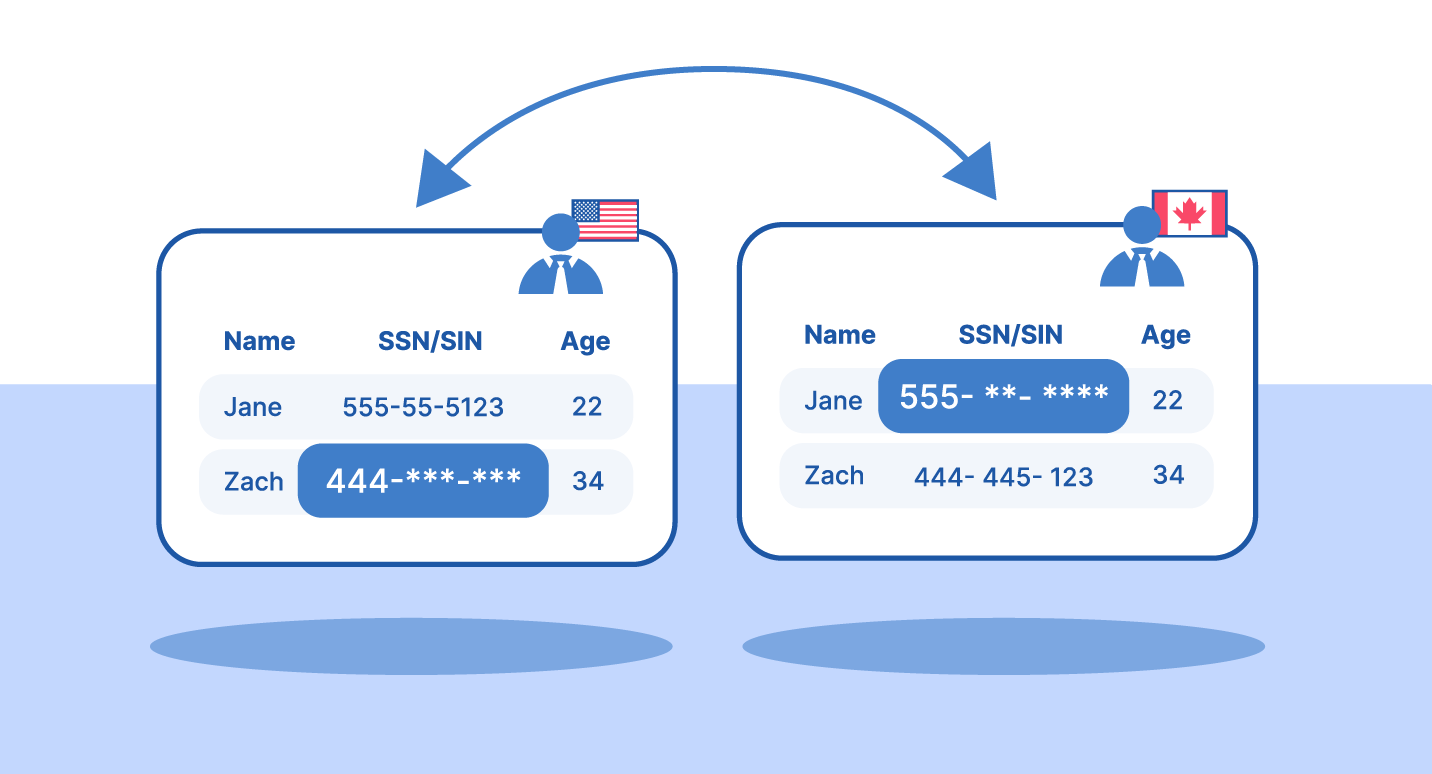
Masking is often irreversible. It's ideal for test environments, analytics, and training systems.
Tokenization replaces sensitive data with a non-sensitive placeholder. The original data is stored in a secure vault. The token has no mathematical relationship to the original value.
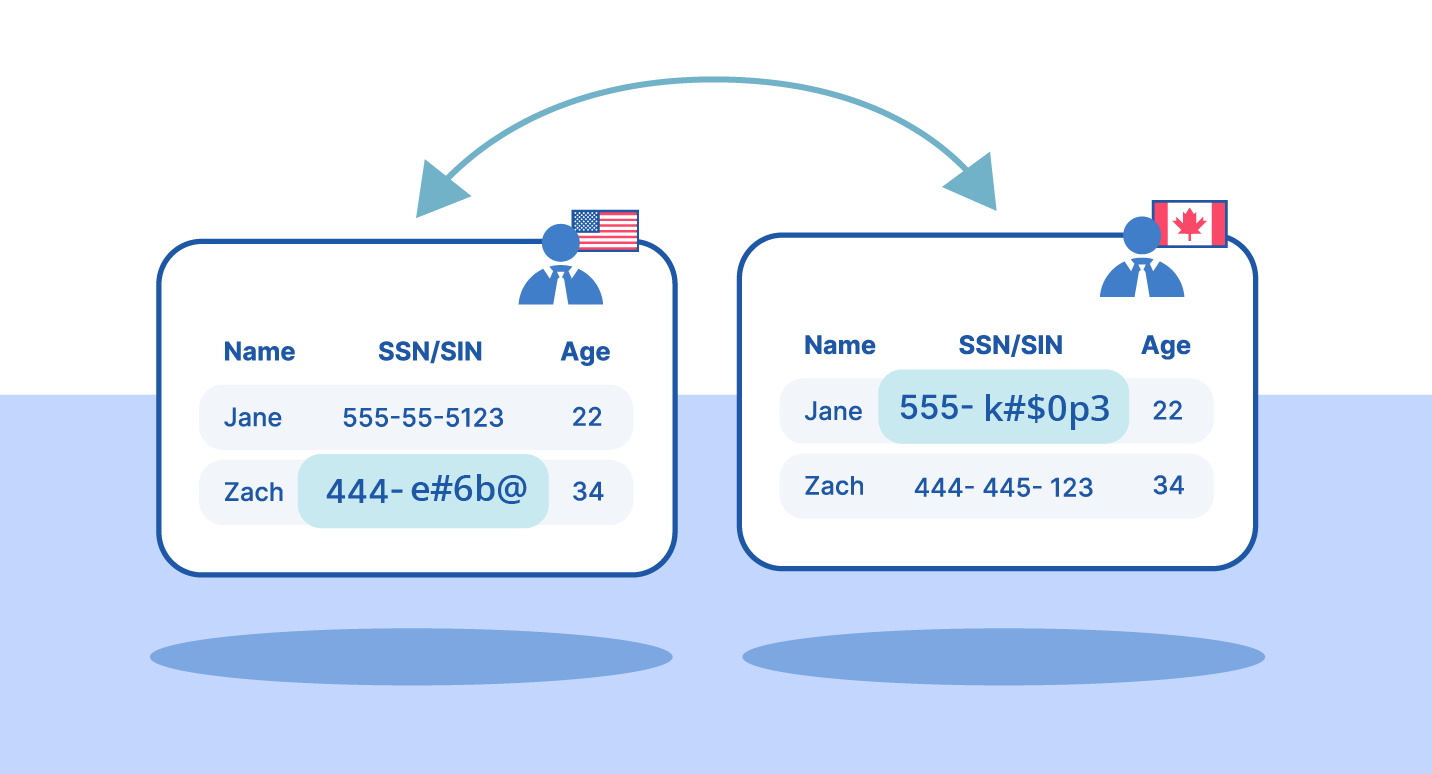
If attackers breach the database, they get tokens – not usable data.
Tokenization vs encryption vs masking: each protects data differently. Tokenization removes data from systems. Encryption protects data in place. Masking hides data for specific use cases.
Encryption transforms data using a cryptographic algorithm. It protects data at rest (stored on disk) and in transit (moving across networks).
Key Characteristics:
Encryption alone doesn't stop insider threats or misuse by authorized users.
FPE encrypts data while maintaining its original format and length. A 16-digit credit card number remains a 16-digit string after encryption. This allows protection without application changes.
FPE is ideal when:
Granular access controls limit who can view unmasked data. This includes role-based access control (RBAC), attribute-based access control (ABAC), and least privilege enforcement.
Advanced platforms add anomaly detection. Machine learning identifies unusual data access patterns that could indicate a breach or insider threat.
The platform logs all data access attempts, policy enforcement actions, and security events. These logs generate reports for compliance audits and incident response.
Choosing between FPE and tokenization depends on your use case.
When to use FPE: Legacy system compatibility, high-throughput scenarios, one-way data flows.
When to use tokenization: PCI DSS scope reduction, cross-system consistency, complete sensitive data removal.
Technical architects evaluating data protection platforms should assess these factors:
Processing petabyte-scale databases with billions of rows requires horizontal scalability. The platform must process data concurrently without introducing unacceptable latency.
Ask vendors for specific latency numbers for FPE and tokenization operations under peak load.
The platform should support your infrastructure:
Modern enterprises use hundreds of applications. The platform should integrate with:
Platforms with a network-layer architecture can intercept and protect data in transit without requiring API integrations for each system.
In sharded or distributed databases, the same sensitive value must resolve to the same token across all systems. Deterministic tokenization guarantees this consistency.
Without referential integrity, joins, deduplication, and analytics break.
Evaluate the resources required to operate the platform:
Platforms with no-code, agentless architectures minimize operational overhead.
The platform should directly support your compliance requirements:
Use a data protection platform when you need to:
DSPM (Data Security Posture Management) tools and data protection platforms solve different problems.
DSPM tools tell you where sensitive data exists and alert you to risks. Data protection platforms neutralize that data so breaches don't matter.
Many organizations use both. DSPM provides visibility. Data protection platforms provide control.
Several platforms address enterprise data protection requirements. Here's how they compare:
DataStealth uses an agentless, network-layer architecture. It intercepts data in transit and protects it without agents, code changes, or API integrations.
Key strengths:
DataStealth is ideal for complex environments with legacy systems, SaaS data sprawl, and high-throughput requirements.
Thales CipherTrust Manager provides centralized key management and encryption across hybrid environments. It offers database encryption, application encryption, and tokenization with strong HSM integration.
Key strengths:
Varonis specializes in data security posture management for unstructured data. It identifies sensitive data in file shares, SharePoint, and cloud storage while monitoring access patterns.
Key strengths:
Baffle provides database and application encryption without code changes. It focuses on protecting data at rest, in memory, and in use within databases.
Key strengths:
Cyera is an AI-powered DSPM platform. It discovers and classifies sensitive data across SaaS, IaaS, and PaaS environments with automated risk assessment.
Key strengths:
Sentra provides DSPM across cloud and on-premises environments. It focuses on sensitive data discovery, classification, and movement detection.
Key strengths:
DataStealth takes a different approach to data protection. Instead of requiring agents, collectors, or API integrations, it operates at the network layer.
DataStealth sits inline and inspects network traffic at the packet level. It extracts sensitive data and replaces it with tokens or masked values in real-time. The original data never reaches the destination system.
Deployment is simple: A DNS change routes traffic through DataStealth. No application modifications. No agents to install.
Bilal is the Content Strategist at DataStealth. He's a recognized defence and security analyst who's researching the growing importance of cybersecurity and data protection in enterprise-sized organizations.